The Profiler system allows SSO enabled authentication against Microsoft 365 Azure. The document outlines the required steps to enroll Profiler as an Enterprise Application in Microsoft Azure for single sign-on for your Profiler instance.
Profiler uses the Microsoft Identity Platform using modern OpenID & OAuth 2.0 to verify the user against Azure AD. It does NOT use the legacy SAML protocol.
Key Information
- Login Redirect URI https://sso.profilersystem.com/SSO/AuthMS/
- Front-channel logout URL https://sso.profilersystem.com/Logout/
- Permissions needed for Microsoft Graph are User.Read – Sign in and read user Profile
Enable SSO inside Profiler
To allow Profiler to work with Azure AD – go to Setup > System Wide Settings and in the General Options choose/tick/enable Use Microsoft/Office365 Single Sign-On for Authentication.
Once enabled this will add the Login with Microsoft 365 on your login screen for Profiler.
Automatically add the application to your Azure AD enterprise apps
- Go to your Profiler instance login page
- Click Login with Microsoft 365
Enterprise Application Setup
- From Enterprise Applications click Add New Application
- Search for Profiler Software in the Azure AD Gallery (you can also add this by going to the “Contact Profiler Support” stage below)
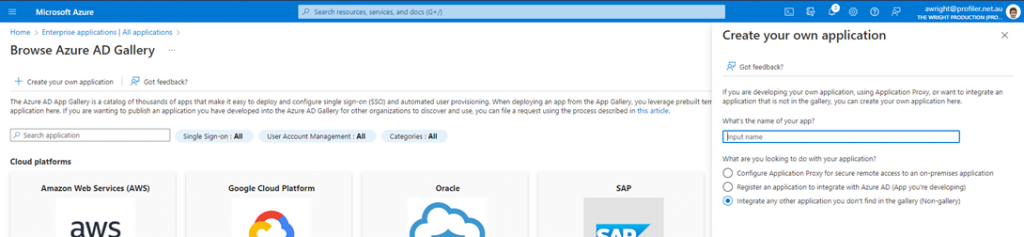
- Add this to your Azure Application stack following the instructions
- Contact Profiler Support on [email protected] to organise an account to be added to the Profiler SSO system that can be logged in as a test (ie. [email protected]) for SSO. This account on logon will check and install the Azure Application into the Active Directory Applications.
- You will then be able to log on to the Profiler system and check (or install) to Azure Profiler App for SSO
- Profiler Support can help with further details on [email protected]
- You can customise any features / permissions on the app inside the Azure AD applications as Profiler only uses the User.Read permission to get the email address UPN of the user for verification.
OpenID / Connect Workflow for Authentication with Profiler CRM
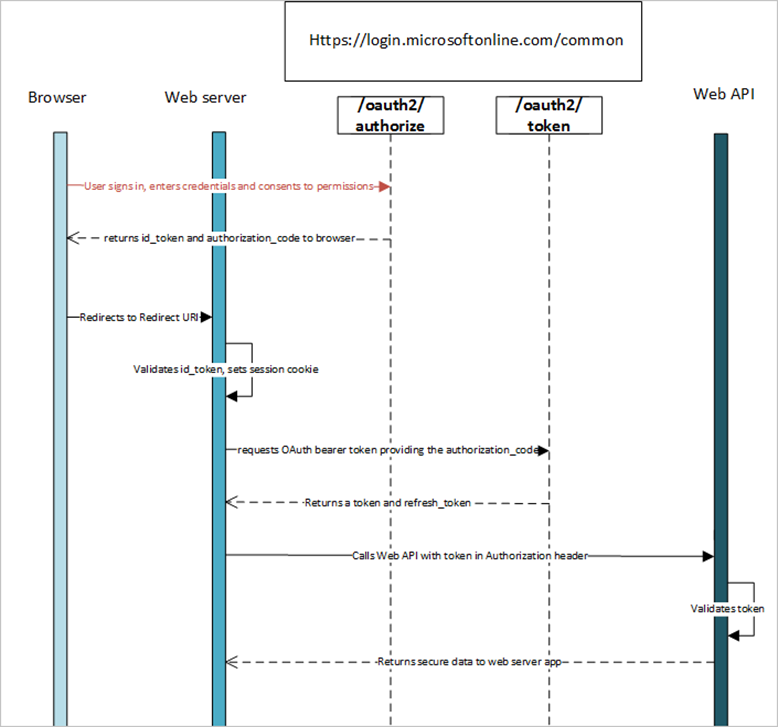
Username SSO Map (inside Profiler)
Using a high-level access user (or raising a ticket with Profiler Support) you can set up user management using SSO at Setup > User Management
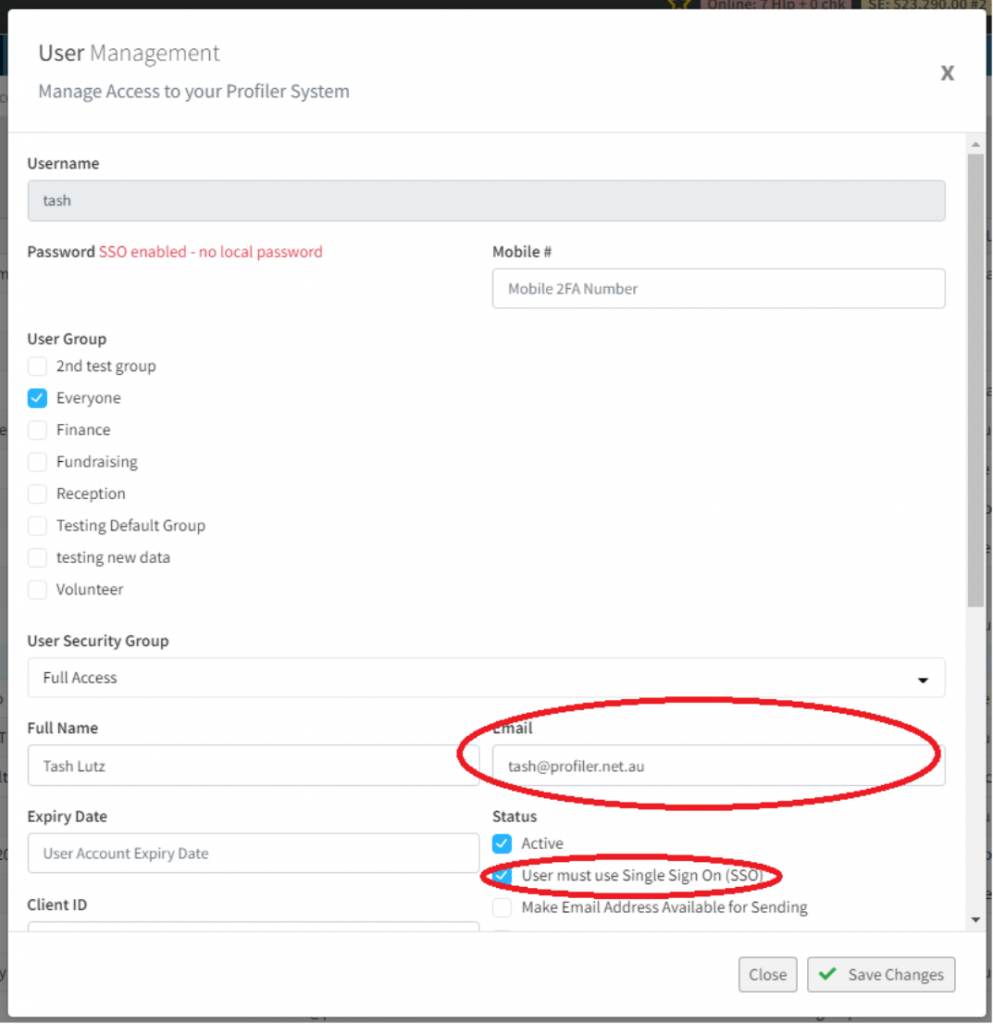
- For users using SSO, ensure the Email field matches that as found on the Azure AD profile (as part of the User.Read) permissions
- Tick the User Must Use Single Sign On – this enforces the user for SSO. This user will no longer be able to log on with a standard username and password, and must use SSO – you can find more details on that process here
- Once you are sure this is all operational, go to Setup > System Wide Settings and in the General Options tick/enable the Enforce SSO Login – this will enforce all users to log in via SSO, there will be no option for non-SSO logon.
